********************************************************************************
2024-10-26 tomcat 8.5 도메인을 https 설정
********************************************************************************
service tomcat stop
cd /etc/letsencrypt/live
rm -rf www.jobtoy.com-0015/
certbot-auto certonly -d www.jobtoy.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: Spin up a temporary webserver (standalone)
2: Place files in webroot directory (webroot)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 1
cd www.jobtoy.com-0016/
ls
README cert.pem chain.pem fullchain.pem privkey.pem
openssl rsa -in privkey.pem -text > www.jobtoy.com.key
openssl x509 -inform PEM -in fullchain.pem -out www.jobtoy.com.crt
openssl pkcs12 -export -in www.jobtoy.com.crt -inkey www.jobtoy.com.key -out www.jobtoy.com.p12 -name tomcat
ls
README chain.pem privkey.pem www.jobtoy.com.key
cert.pem fullchain.pem www.jobtoy.com.crt www.jobtoy.com.p12
openssl req -new -key www.jobtoy.com.key -out www.jobtoy.com.csr
keytool -importkeystore -srckeystore www.jobtoy.com.p12 -srcstoretype pkcs12 -destkeystore www.jobtoy.com.jks -deststoretype jks
ls
README chain.pem privkey.pem www.jobtoy.com.csr www.jobtoy.com.key
cert.pem fullchain.pem www.jobtoy.com.crt www.jobtoy.com.jks www.jobtoy.com.p12
nano /usr/local/server/apache-tomcat-8.5.73/conf/server.xml
service tomcat start
********************************************************************************
2024-7-19 tomcat 8.5 새 도메인을 https에 맞추어 추가함
********************************************************************************
* 사용한 명령어 모음
cd /etc/letsencrypt/
certbot-auto certonly -d batteryall.co.kr
cd live
cd batteryall.co.kr/
openssl rsa -in privkey.pem -text > batteryall.co.kr.key
openssl x509 -inform PEM -in fullchain.pem -out batteryall.co.kr.crt
openssl pkcs12 -export -in batteryall.co.kr.crt -inkey batteryall.co.kr.key -out batteryall.co.kr.p12 -name tomcat
openssl req -new -key batteryall.co.kr.key -out batteryall.co.kr.csr
keytool -importkeystore -srckeystore batteryall.co.kr.p12 -srcstoretype pkcs12 -destkeystore batteryall.co.kr.jks -deststoretype jks
keytool -list -keystore batteryall.co.kr.jks
[root@labj /]# service tomcat stop
Using CATALINA_BASE: /usr/local/server/apache-tomcat-8.5.73
Using CATALINA_HOME: /usr/local/server/apache-tomcat-8.5.73
Using CATALINA_TMPDIR: /usr/local/server/apache-tomcat-8.5.73/temp
Using JRE_HOME: /usr/local/java/jdk1.8.0_111
Using CLASSPATH: /usr/local/server/apache-tomcat-8.5.73/bin/bootstrap.jar:/usr/local/server/apache-tomcat-8.5.73/bin/tomcat-juli.jar
Using CATALINA_OPTS:
[root@labj /]# cd /etc/letsencrypt/
[root@labj letsencrypt]# certbot-auto certonly -d www.vape.co.kr
Your system is not supported by certbot-auto anymore.
certbot-auto and its Certbot installation will no longer receive updates.
You will not receive any bug fixes including those fixing server compatibility
or security problems.
Please visit https://certbot.eff.org/ to check for other alternatives.
Saving debug log to /var/log/letsencrypt/letsencrypt.log
How would you like to authenticate with the ACME CA?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: Spin up a temporary webserver (standalone)
2: Place files in webroot directory (webroot)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 1
Plugins selected: Authenticator standalone, Installer None
Requesting a certificate for www.vape.co.kr
Performing the following challenges:
http-01 challenge for www.vape.co.kr
Waiting for verification...
Cleaning up challenges
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/www.vape.co.kr/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/www.vape.co.kr/privkey.pem
Your cert will expire on 2024-10-17. To obtain a new or tweaked
version of this certificate in the future, simply run certbot-auto
again. To non-interactively renew *all* of your certificates, run
"certbot-auto renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
[root@labj letsencrypt]# cd live
[root@labj live]# ls
README www.jobtoy.com-0013 www.jobtoy.com.key www.namuwnamu.com www.vape.co.kr
[root@labj live]# cd www.vape.co.kr/
[root@labj www.vape.co.kr]# openssl rsa -in privkey.pem -text > www.vape.co.kr.key
writing RSA key
[root@labj www.vape.co.kr]# openssl x509 -inform PEM -in fullchain.pem -out www.vape.co.kr.crt
[root@labj www.vape.co.kr]# openssl pkcs12 -export -in www.vape.co.kr.crt -inkey www.vape.co.kr.key -out www.vape.co.kr.p12 -name tomcat
Enter Export Password:
Verifying - Enter Export Password:
[root@labj www.vape.co.kr]# openssl req -new -key www.vape.co.kr.key -out www.vape.co.kr.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:kr
State or Province Name (full name) []:vape
Locality Name (eg, city) [Default City]:Seoul
Organization Name (eg, company) [Default Company Ltd]:vape
Organizational Unit Name (eg, section) []:vape
Common Name (eg, your name or your server's hostname) []:vape
Email Address []:hnamju@gmail.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:****!
An optional company name []:vape
[root@labj www.vape.co.kr]# keytool -importkeystore -srckeystore www.vape.co.kr.p12 -srcstoretype pkcs12 -destkeystore www.vape.co.kr.jks -de ststoretype jks
대상 키 저장소 비밀번호 입력:
새 비밀번호 다시 입력:
소스 키 저장소 비밀번호 입력:
tomcat 별칭에 대한 항목이 성공적으로 임포트되었습니다.
임포트 명령 완료: 성공적으로 임포트된 항목은 1개, 실패하거나 취소된 항목은 0개입니다.
[root@labj www.vape.co.kr]# keytool -list -keystore www.vape.co.kr.jks
키 저장소 비밀번호 입력:
키 저장소 유형: JKS
키 저장소 제공자: SUN
키 저장소에 1개의 항목이 포함되어 있습니다.
tomcat, 2024. 7. 19, PrivateKeyEntry,
인증서 지문(SHA1): E7:A6:7D:53:81:51:82:0A:35:C4:6D:72:ED:7D:EE:70:A1:CF:22:3C
[root@labj www.vape.co.kr]#
********************************************************************************
2024-7-17 tomcat 8.5 SSL 사용하기 위해서 ( JKS , PKCS12, PEM ) HTTP/2 적용
-> https://xinet.kr/?p=1674 사이트 내용 참고해서 적용함
********************************************************************************
[root@labj logs]# cd /etc/letsencrypt/live/www.jobtoy.com.com-0013/
You have new mail in /var/spool/mail/root
[root@labj www.jobtoy.com.com-0013]# ls -al
합계 28
drwxr-xr-x 2 root tomcat 4096 2024-06-11 02:48 .
drwxrwxrwx 3 root tomcat 4096 2024-06-10 23:47 ..
-rw-r--r-- 1 root tomcat 692 2024-06-10 23:47 README
lrwxrwxrwx 1 root tomcat 43 2024-06-11 02:48 cert.pem -> ../../archive/www.jobtoy.com-0013/cert3.pem
lrwxrwxrwx 1 root tomcat 44 2024-06-11 02:48 chain.pem -> ../../archive/www.jobtoy.com-0013/chain3.pem
lrwxrwxrwx 1 root tomcat 48 2024-06-11 02:48 fullchain.pem -> ../../archive/www.jobtoy.com-0013/fullchain3.pem
lrwxrwxrwx 1 root tomcat 46 2024-06-11 02:48 privkey.pem -> ../../archive/www.jobtoy.com-0013/privkey3.pem
-rw-r--r-- 1 root tomcat 1769 2024-06-11 02:51 www.jobtoy.com.com.crt
-rw-r--r-- 1 root tomcat 5674 2024-06-11 02:51 www.jobtoy.com.com.key
-rw-r--r-- 1 root tomcat 2922 2024-06-11 02:52 www.jobtoy.com.com.p12
[root@labj www.jobtoy.com.com-0013]# openssl req -new -key www.jobtoy.com.com.key -out www.jobtoy.com.com.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:ko
State or Province Name (full name) []:Seoul
Locality Name (eg, city) [Default City]:Paju
Organization Name (eg, company) [Default Company Ltd]:jobtoy
Organizational Unit Name (eg, section) []:jobtoy
Common Name (eg, your name or your server's hostname) []:www.jobtoy.com.com
Email Address []:hnamju@gmail.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:****!
An optional company name []:jobtoy
You have new mail in /var/spool/mail/root
[root@labj www.jobtoy.com.com-0013]# keytool -importkeystore -srckeystore www.jobtoy.com.com.p12 -srcstoretype pkcs12 -destkeystore www.jobtoy.com.com.jks -deststoretype jks
대상 키 저장소 비밀번호 입력:
새 비밀번호 다시 입력:
소스 키 저장소 비밀번호 입력:
tomcat 별칭에 대한 항목이 성공적으로 임포트되었습니다.
임포트 명령 완료: 성공적으로 임포트된 항목은 1개, 실패하거나 취소된 항목은 0개입니다.
[root@labj www.jobtoy.com.com-0013]# ls
README chain.pem privkey.pem www.jobtoy.com.com.csr www.jobtoy.com.com.key
cert.pem fullchain.pem www.jobtoy.com.com.crt www.jobtoy.com.com.jks www.jobtoy.com.com.p12
[root@labj www.jobtoy.com.com-0013]# keytool -list -keystore www.jobtoy.com.com.jks
키 저장소 비밀번호 입력:
키 저장소 유형: JKS
키 저장소 제공자: SUN
키 저장소에 1개의 항목이 포함되어 있습니다.
tomcat, 2024. 7. 17, PrivateKeyEntry,
인증서 지문(SHA1): 5C:EC:D4:19:BF:AC:D2:80:15:33:82:B0:8C:71:CB:27:28:AA:7E:09
[root@labj www.jobtoy.com.com-0013]# ls
README chain.pem privkey.pem www.jobtoy.com.com.csr www.jobtoy.com.com.key
cert.pem fullchain.pem www.jobtoy.com.com.crt www.jobtoy.com.com.jks www.jobtoy.com.com.p12
실행하고 tomcat에서 server.xml을 다음처럼 변경하고 웹사이트 접속했는데 정상적으로 처리됨
********************************************************************************
2024-3-19 파일 삭제 없이 다음 순서대로 명령을 치면 3개월 업데이트 됨
********************************************************************************
[root@labj ~]# service tomcat stop
[root@labj ~]# cd /etc/letsencrypt/</b
[root@labj letsencrypt]# certbot-auto certonly -d www.jobtoy.com
...
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: Spin up a temporary webserver (standalone)
2: Place files in webroot directory (webroot)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 1
...
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: Keep the existing certificate for now
2: Renew & replace the cert (may be subject to CA rate limits)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2
[root@labj letsencrypt]# cd live
[root@labj live]# ls
README www.jobtoy.com-0013 www.jobtoy.com.key
[root@labj live]# cd www.jobtoy.com-0013/
[root@labj www.jobtoy.com-0013]# openssl rsa -in privkey.pem -text > www.jobtoy.com.key
[root@labj www.jobtoy.com-0013]# openssl x509 -inform PEM -in fullchain.pem -out www.jobtoy.com.crt
[root@labj www.jobtoy.com-0013]# openssl pkcs12 -export -in www.jobtoy.com.crt -inkey www.jobtoy.com.key -out www.jobtoy.com.p12 -name tomcat
Enter Export Password:
Verifying - Enter Export Password:
[root@labj www.jobtoy.com-0013]# service tomcat start
login as: root
root@222.122.203.217's password:
Last login: Mon Jun 10 23:31:59 2024 from 221.155.196.82
[root@labj ~]# service tomcat stop
Using CATALINA_BASE: /usr/local/server/apache-tomcat-8.0.41
Using CATALINA_HOME: /usr/local/server/apache-tomcat-8.0.41
Using CATALINA_TMPDIR: /usr/local/server/apache-tomcat-8.0.41/temp
Using JRE_HOME: /usr/local/java/jdk1.8.0_111
Using CLASSPATH: /usr/local/server/apache-tomcat-8.0.41/bin/bootstrap.jar:/usr/local/server/apache-tomcat-8.0.41/bin/tomcat-juli.jar
[root@labj ~]# cd /etc/letsencrypt/
You have new mail in /var/spool/mail/root
[root@labj letsencrypt]# certbot-auto certonly -d www.jobtoy.com
Your system is not supported by certbot-auto anymore.
certbot-auto and its Certbot installation will no longer receive updates.
You will not receive any bug fixes including those fixing server compatibility
or security problems.
Please visit https://certbot.eff.org/ to check for other alternatives.
Saving debug log to /var/log/letsencrypt/letsencrypt.log
How would you like to authenticate with the ACME CA?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: Spin up a temporary webserver (standalone)
2: Place files in webroot directory (webroot)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 1
Plugins selected: Authenticator standalone, Installer None
Cert not yet due for renewal
You have an existing certificate that has exactly the same domains or certificate name you requested and isn't close to expiry.
(ref: /etc/letsencrypt/renewal/www.jobtoy.com-0013.conf)
What would you like to do?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: Keep the existing certificate for now
2: Renew & replace the cert (may be subject to CA rate limits)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2
Renewing an existing certificate for www.jobtoy.com
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/www.jobtoy.com-0013/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/www.jobtoy.com-0013/privkey.pem
Your cert will expire on 2024-09-08. To obtain a new or tweaked
version of this certificate in the future, simply run certbot-auto
again. To non-interactively renew *all* of your certificates, run
"certbot-auto renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
[root@labj letsencrypt]# ls
accounts archive csr keys live renewal renewal-hooks
You have new mail in /var/spool/mail/root
[root@labj letsencrypt]# cd live
[root@labj live]# ls
README www.jobtoy.com-0013 www.jobtoy.com.key
[root@labj live]# cd www.jobtoy.com-0013/
[root@labj www.jobtoy.com-0013]# ls
README chain.pem privkey.pem www.jobtoy.com.key
cert.pem fullchain.pem www.jobtoy.com.crt www.jobtoy.com.p12
[root@labj www.jobtoy.com-0013]# openssl rsa -in privkey.pem -text > www.jobtoy.com.key
writing RSA key
[root@labj www.jobtoy.com-0013]# openssl x509 -inform PEM -in fullchain.pem -out www.jobtoy.com.crt
[root@labj www.jobtoy.com-0013]# openssl pkcs12 -export -in www.jobtoy.com.crt -inkey www.jobtoy.com.key -out www.jobtoy.com.p12 -name tomcat
Enter Export Password:
Verifying - Enter Export Password:
[root@labj www.jobtoy.com-0013]# service tomcat start
Using CATALINA_BASE: /usr/local/server/apache-tomcat-8.0.41
Using CATALINA_HOME: /usr/local/server/apache-tomcat-8.0.41
Using CATALINA_TMPDIR: /usr/local/server/apache-tomcat-8.0.41/temp
Using JRE_HOME: /usr/local/java/jdk1.8.0_111
Using CLASSPATH: /usr/local/server/apache-tomcat-8.0.41/bin/bootstrap.jar:/usr/local/server/apache-tomcat-8.0.41/bin/tomcat-juli.jar
Tomcat started.
You have new mail in /var/spool/mail/root
[root@labj www.jobtoy.com-0013]#
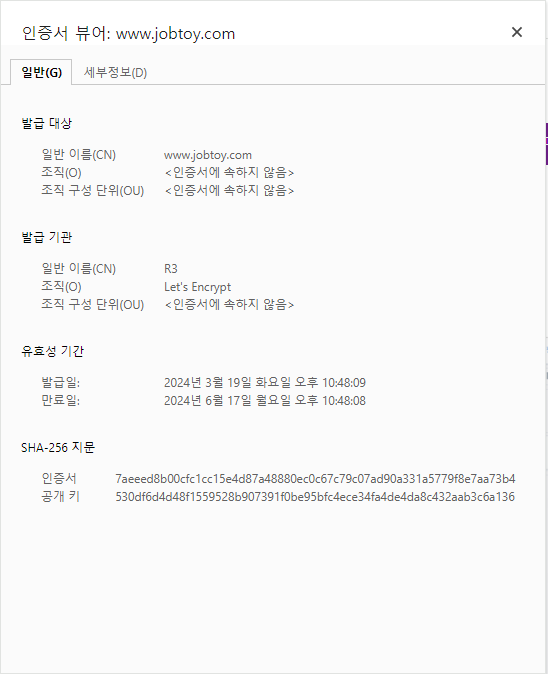
*******************************************************
2023-2-5 yum 업데이트 오류 해결
*******************************************************
echo "https://vault.centos.org/6.10/os/x86_64/" > /var/cache/yum/x86_64/6/base/mirrorlist.txt
echo "http://vault.centos.org/6.10/extras/x86_64/" > /var/cache/yum/x86_64/6/extras/mirrorlist.txt
echo "http://vault.centos.org/6.10/updates/x86_64/" > /var/cache/yum/x86_64/6/updates/mirrorlist.txt
yum update
*******************************************************
2022-8-20 인증서 설치하기
*******************************************************
톰캣 서버 정지
service tomcat stop
cd /etc/letsencrypt/live
기존 파일 삭제
[root@labj live]# rm -rf www.jobtoy.com-0003
*************************************************
certbot-auto 지원이 제대로 안 됨
이전버전을 설치를 진행함
* 인증서 새로 설치
[root@labj live]# cd /root
[root@labj ~]# wget https://dl.eff.org/certbot-auto -P /usr/local/bin
[root@labj ~]# chmod a+x /usr/local/bin/certbot-auto
[root@labj ~]# certbot-auto certonly -d www.jobtoy.com
*************************************************
* 이전버전 설치
cd /usr/bin
wget -O certbot-auto https://raw.githubusercontent.com/certbot/certbot/1.10.x/certbot-auto
chmod ug+x certbot-auto
certbot-auto --install-only --no-self-upgrade -n
* 버전이 1.10.1 로 나오면 정상임
/usr/bin/certbot-auto --version
...
[root@labj bin]# cd /etc/letsencrypt
[root@labj letsencrypt]# certbot-auto certonly -d www.jobtoy.com
Saving debug log to /var/log/letsencrypt/letsencrypt.log
How would you like to authenticate with the ACME CA?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: Spin up a temporary webserver (standalone)
2: Place files in webroot directory (webroot)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 1
Plugins selected: Authenticator standalone, Installer None
Obtaining a new certificate
...
"certbot-auto renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
[root@labj letsencrypt]# cd live
[root@labj live]# ls
README www.jobtoy.com-0007 www.jobtoy.com.key
[root@labj live]# cd www.jobtoy.com-007
[root@labj www.jobtoy.com]# openssl rsa -in privkey.pem -text > www.jobtoy.com.key
writing RSA key
[root@labj www.jobtoy.com]# openssl x509 -inform PEM -in fullchain.pem -out www.jobtoy.com.crt
[root@labj www.jobtoy.com]# openssl pkcs12 -export -in www.jobtoy.com.crt -inkey www.jobtoy.com.key -out www.jobtoy.com.p12 -name tomcat
Enter Export Password: ****
Verifying - Enter Export Password: ****
* 인증서 파일 생성 끝
* 톰캣 server.xml letsencrypt 경로 수정
[root@labj www.jobtoy.com]# sudo nano /usr/local/server/apache-tomcat-8.0.41/conf/server.xml
...
org.apache.coyote.http11.Http11NioProtocol"
maxThreads="150" SSLEnabled="true" scheme="https" secure="true"
clientAuth="false" sslProtocol="TLS"
keystoreFile="/etc/letsencrypt/live/www.jobtoy.com/www.jobtoy.com.p12"
keystoreType="PKCS12" keystorePass="********"
/>
...
[root@labj www.jobtoy.com]# cd /usr/local/server/apache-tomcat-8.0.41/
[root@labj www.jobtoy.com]# cd /usr/local/server/apache-tomcat-8.0.41/logs
[root@labj logs]# rm -rf *
[root@labj logs]# ls
[root@labj logs]# service tomcat start
수동으로 3개월마다 적용
*******************************************************
2021-3-15 인증서 설치하기
*******************************************************
톰캣 서버 정지
service tomcat stop
cd /etc/letsencrypt/live
기존 파일 삭제
rm -rf www.jobtoy.com
* 인증서 새로 설치
[root@labj ~]# wget https://dl.eff.org/certbot-auto -P /usr/local/bin
[root@labj ~]# chmod a+x /usr/local/bin/certbot-auto
[root@labj ~]# certbot-auto certonly -d www.jobtoy.com
...
[root@labj letsencrypt]# certbot-auto certonly -d www.jobtoy.com
Saving debug log to /var/log/letsencrypt/letsencrypt.log
How would you like to authenticate with the ACME CA?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: Spin up a temporary webserver (standalone)
2: Place files in webroot directory (webroot)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 1
Plugins selected: Authenticator standalone, Installer None
Obtaining a new certificate
...
"certbot-auto renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
[root@labj letsencrypt]# pwd
/etc/letsencrypt/live
[root@labj letsencrypt]# cd /etc/letsencrypt/live/www.jobtoy.com/
[root@labj www.jobtoy.com]# openssl rsa -in privkey.pem -text > www.jobtoy.com.key
writing RSA key
[root@labj www.jobtoy.com]# openssl x509 -inform PEM -in fullchain.pem -out www.jobtoy.com.crt
[root@labj www.jobtoy.com]# openssl pkcs12 -export -in www.jobtoy.com.crt -inkey www.jobtoy.com.key -out www.jobtoy.com.p12 -name tomcat
Enter Export Password: ****
Verifying - Enter Export Password: ****
* 인증서 파일 생성 끝
[root@labj www.jobtoy.com]# sudo nano /usr/local/server/apache-tomcat-8.0.41/conf/server.xml
...
org.apache.coyote.http11.Http11NioProtocol"
maxThreads="150" SSLEnabled="true" scheme="https" secure="true"
clientAuth="false" sslProtocol="TLS"
keystoreFile="/etc/letsencrypt/live/www.jobtoy.com/www.jobtoy.com.p12"
keystoreType="PKCS12" keystorePass="********"
/>
...
[root@labj www.jobtoy.com]# cd /usr/local/server/apache-tomcat-8.0.41/logs
[root@labj logs]# rm -rf *
[root@labj logs]# ls
[root@labj logs]# service tomcat start
수동으로 3개월마다 적용
*******************************************************
2020-12-09 인증서 설치하기
*******************************************************
톰캣 서버 정지 후
/etc/letsencrypt/live/www.jobtoy.com 삭제후
[root@labj ~]# wget https://dl.eff.org/certbot-auto -P /usr/local/bin
[root@labj ~]# chmod a+x /usr/local/bin/certbot-auto
[root@labj ~]# certbot-auto certonly -d www.jobtoy.com
...
[root@labj letsencrypt]# certbot-auto certonly -d www.jobtoy.com
Saving debug log to /var/log/letsencrypt/letsencrypt.log
How would you like to authenticate with the ACME CA?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: Spin up a temporary webserver (standalone)
2: Place files in webroot directory (webroot)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 1
Plugins selected: Authenticator standalone, Installer None
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for www.jobtoy.com
Waiting for verification...
Cleaning up challenges
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/www.jobtoy.com/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/www.jobtoy.com/privkey.pem
Your cert will expire on 2020-06-26. To obtain a new or tweaked
version of this certificate in the future, simply run certbot-auto
again. To non-interactively renew *all* of your certificates, run
"certbot-auto renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
[root@labj letsencrypt]#
[root@labj letsencrypt]# pwd
/etc/letsencrypt
[root@labj letsencrypt]# ls /etc/letsencrypt/live
README www.jobtoy.com
[root@labj letsencrypt]# ls /etc/letsencrypt/live/www.jobtoy.com/
cert.pem chain.pem fullchain.pem privkey.pem README
[root@labj letsencrypt]#
*******************************************************
2020-03-28 인증서 갱신 설정하기
*******************************************************
서버를 끈 후에 설정을 적용합니다.
다시 서버를 켜니까 정상으로 3개월 연장이 적용되었습니다.
[root@labj www.jobtoy.com]# oopenssl rsa -in privkey.pem -text > www.jobtoy.com.key
-bash: oopenssl: command not found
[root@labj www.jobtoy.com]# openssl rsa -in privkey.pem -text > www.jobtoy.com.key
writing RSA key
[root@labj www.jobtoy.com]# ls
cert.pem chain.pem fullchain.pem privkey.pem README www.jobtoy.com.key
[root@labj www.jobtoy.com]# openssl x509 -inform PEM -in fullchain.pem -out www.jobtoy.com.crt
[root@labj www.jobtoy.com]# ls
cert.pem fullchain.pem README www.jobtoy.com.key
chain.pem privkey.pem www.jobtoy.com.crt
[root@labj www.jobtoy.com]# openssl pkcs12 -export -in www.jobtoy.com.crt -inkey www.jobtoy.com.key -out www.jobtoy.com.p12 -name tomcat
Enter Export Password:
Verifying - Enter Export Password:
[root@labj www.jobtoy.com]# ls
cert.pem fullchain.pem README www.jobtoy.com.key
chain.pem privkey.pem www.jobtoy.com.crt www.jobtoy.com.p12
[root@labj www.jobtoy.com]# sudo nano /usr/local/server/apache-tomcat-8.0.41/conf/server.xml
...
org.apache.coyote.http11.Http11NioProtocol"
maxThreads="150" SSLEnabled="true" scheme="https" secure="true"
clientAuth="false" sslProtocol="TLS"
keystoreFile="/etc/letsencrypt/live/www.jobtoy.com/www.jobtoy.com.p12"
keystoreType="PKCS12" keystorePass="********"
/>
...
[root@labj www.jobtoy.com]# cd /usr/local/server/apache-tomcat-8.0.41/logs
[root@labj logs]# rm -rf *
[root@labj logs]# ls
[root@labj logs]# service tomcat start
자동 설정은 하기 어려워서
수동으로 3개월마다 적용해야 할 것으로 보임
* 아래 방법은 다음번에 적용 테스트를 진행해 보도록 해야겠습니다.
cent os 톰캣(tomcat) Letsencrypt SSL 인증서 적용
인증서 자동갱신 : https://devlog.jwgo.kr/2019/04/16/how-to-lets-encrypt-ssl-renew/
*******************************************************
2020-03-28 인증서 설치하기
*******************************************************
[root@labj ~]# wget https://dl.eff.org/certbot-auto -P /usr/local/bin
--2020-03-28 19:17:47-- https://dl.eff.org/certbot-auto
Resolving dl.eff.org... 151.101.40.201, 2a04:4e42:2e::201
Connecting to dl.eff.org|151.101.40.201|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 80073 (78K) [application/octet-stream]
Saving to: “/usr/local/bin/certbot-auto”
100%[======================================>] 80,073 244K/s in 0.3s
2020-03-28 19:17:49 (244 KB/s) - “/usr/local/bin/certbot-auto” saved [80073/80073]
[root@labj ~]# chmod a+x /usr/local/bin/certbot-auto
[root@labj ~]# firewall-cmd --add-service https --permanent
-bash: firewall-cmd: command not found
[root@labj ~]# firewall-cmd --add -service https --permanent
-bash: firewall-cmd: command not found
[root@labj ~]# firewall -cmd --add -service https --permanent
-bash: firewall: command not found
[root@labj ~]# certbot-auto certonly -d www.jobtoy.com
Bootstrapping dependencies for Legacy RedHat-based OSes that will use Python3... (you can skip this with --no-bootstrap)
yum is hashed (/usr/bin/yum)
To use Certbot on this operating system, packages from the SCL repository need to be installed.
Loaded plugins: fastestmirror, security
Setting up Install Process
Loading mirror speeds from cached hostfile
* base: mirror.navercorp.com
* extras: mirror.navercorp.com
* rpmforge: apt.sw.be
* updates: mirror.navercorp.com
No package available.
No package available.
Resolving Dependencies
--> Running transaction check
---> Package centos-release-scl.noarch 10:7-4.el6.centos will be installed
--> Processing Dependency: centos-release-scl-rh for package: 10:centos-release-scl-7-4.el6.centos.noarch
--> Running transaction check
---> Package centos-release-scl-rh.noarch 0:2-4.el6.centos will be installed
--> Finished Dependency Resolution
Dependencies Resolved
================================================================================
Package Arch Version Repository Size
================================================================================
Installing:
centos-release-scl noarch 10:7-4.el6.centos extras 12 k
Installing for dependencies:
centos-release-scl-rh noarch 2-4.el6.centos extras 12 k
Transaction Summary
================================================================================
Install 2 Package(s)
Total download size: 24 k
Installed size: 39 k
Is this ok [y/N]: y
Downloading Packages:
(1/2): centos-release-scl-7-4.el6.centos.noarch.rpm | 12 kB 00:00
(2/2): centos-release-scl-rh-2-4.el6.centos.noarch.rpm | 12 kB 00:00
--------------------------------------------------------------------------------
Total 257 kB/s | 24 kB 00:00
Running rpm_check_debug
Running Transaction Test
Transaction Test Succeeded
Running Transaction
Installing : centos-release-scl-rh-2-4.el6.centos.noarch 1/2
Installing : 10:centos-release-scl-7-4.el6.centos.noarch 2/2
Verifying : centos-release-scl-rh-2-4.el6.centos.noarch 1/2
Verifying : 10:centos-release-scl-7-4.el6.centos.noarch 2/2
Installed:
centos-release-scl.noarch 10:7-4.el6.centos
Dependency Installed:
centos-release-scl-rh.noarch 0:2-4.el6.centos
Complete!
yum is hashed (/usr/bin/yum)
Loaded plugins: fastestmirror, security
Setting up Install Process
Loading mirror speeds from cached hostfile
* base: mirror.navercorp.com
* centos-sclo-rh: mirror.navercorp.com
* centos-sclo-sclo: mirror.navercorp.com
* extras: mirror.navercorp.com
* rpmforge: apt.sw.be
* updates: mirror.navercorp.com
Package augeas-libs-1.0.0-10.el6.x86_64 already installed and latest version
Resolving Dependencies
--> Running transaction check
---> Package ca-certificates.noarch 0:2015.2.6-65.0.1.el6_7 will be updated
---> Package ca-certificates.noarch 0:2019.2.32-65.1.el6_10 will be an update
---> Package gcc.x86_64 0:4.4.7-17.el6 will be updated
--> Processing Dependency: gcc = 4.4.7-17.el6 for package: gcc-objc-4.4.7-17.el6.x86_64
--> Processing Dependency: gcc = 4.4.7-17.el6 for package: gcc-gnat-4.4.7-17.el6.x86_64
--> Processing Dependency: gcc = 4.4.7-17.el6 for package: gcc-gfortran-4.4.7-17.el6.x86_64
--> Processing Dependency: gcc = 4.4.7-17.el6 for package: gcc-c++-4.4.7-17.el6.x86_64
---> Package gcc.x86_64 0:4.4.7-23.el6 will be an update
--> Processing Dependency: libgomp = 4.4.7-23.el6 for package: gcc-4.4.7-23.el6.x86_64
--> Processing Dependency: cpp = 4.4.7-23.el6 for package: gcc-4.4.7-23.el6.x86_64
--> Processing Dependency: libgcc >= 4.4.7-23.el6 for package: gcc-4.4.7-23.el6.x86_64
---> Package libffi-devel.x86_64 0:3.0.5-3.2.el6 will be installed
---> Package openssl.x86_64 0:1.0.1e-48.el6_8.3 will be updated
---> Package openssl.x86_64 0:1.0.1e-58.el6_10 will be an update
---> Package openssl-devel.x86_64 0:1.0.1e-48.el6_8.3 will be updated
---> Package openssl-devel.x86_64 0:1.0.1e-58.el6_10 will be an update
---> Package redhat-rpm-config.noarch 0:9.0.3-51.el6.centos will be installed
---> Package rh-python36-python.x86_64 0:3.6.9-2.el6 will be installed
--> Processing Dependency: rh-python36-python-libs(x86-64) = 3.6.9-2.el6 for package: rh-python36-python-3.6.9-2.el6.x86_64
--> Processing Dependency: rh-python36-runtime for package: rh-python36-python-3.6.9-2.el6.x86_64
--> Processing Dependency: rh-python36-python-setuptools for package: rh-python36-python-3.6.9-2.el6.x86_64
--> Processing Dependency: rh-python36-python-pip for package: rh-python36-python-3.6.9-2.el6.x86_64
--> Processing Dependency: libpython3.6m.so.rh-python36-1.0()(64bit) for package: rh-python36-python-3.6.9-2.el6.x86_64
---> Package rh-python36-python-devel.x86_64 0:3.6.9-2.el6 will be installed
--> Processing Dependency: scl-utils-build for package: rh-python36-python-devel-3.6.9-2.el6.x86_64
---> Package rh-python36-python-virtualenv.noarch 0:15.1.0-2.el6 will be installed
--> Running transaction check
---> Package cpp.x86_64 0:4.4.7-17.el6 will be updated
---> Package cpp.x86_64 0:4.4.7-23.el6 will be an update
---> Package gcc-c++.x86_64 0:4.4.7-17.el6 will be updated
--> Processing Dependency: gcc-c++ = 4.4.7-17.el6 for package: gcc-objc++-4.4.7-17.el6.x86_64
---> Package gcc-c++.x86_64 0:4.4.7-23.el6 will be an update
--> Processing Dependency: libstdc++-devel = 4.4.7-23.el6 for package: gcc-c++-4.4.7-23.el6.x86_64
--> Processing Dependency: libstdc++ = 4.4.7-23.el6 for package: gcc-c++-4.4.7-23.el6.x86_64
---> Package gcc-gfortran.x86_64 0:4.4.7-17.el6 will be updated
---> Package gcc-gfortran.x86_64 0:4.4.7-23.el6 will be an update
--> Processing Dependency: libgfortran = 4.4.7-23.el6 for package: gcc-gfortran-4.4.7-23.el6.x86_64
---> Package gcc-gnat.x86_64 0:4.4.7-17.el6 will be updated
---> Package gcc-gnat.x86_64 0:4.4.7-23.el6 will be an update
--> Processing Dependency: libgnat-devel = 4.4.7-23.el6 for package: gcc-gnat-4.4.7-23.el6.x86_64
--> Processing Dependency: libgnat = 4.4.7-23.el6 for package: gcc-gnat-4.4.7-23.el6.x86_64
---> Package gcc-objc.x86_64 0:4.4.7-17.el6 will be updated
---> Package gcc-objc.x86_64 0:4.4.7-23.el6 will be an update
--> Processing Dependency: libobjc = 4.4.7-23.el6 for package: gcc-objc-4.4.7-23.el6.x86_64
---> Package libgcc.x86_64 0:4.4.7-17.el6 will be updated
---> Package libgcc.x86_64 0:4.4.7-23.el6 will be an update
---> Package libgomp.x86_64 0:4.4.7-17.el6 will be updated
---> Package libgomp.x86_64 0:4.4.7-23.el6 will be an update
---> Package rh-python36-python-libs.x86_64 0:3.6.9-2.el6 will be installed
---> Package rh-python36-python-pip.noarch 0:9.0.1-2.el6 will be installed
---> Package rh-python36-python-setuptools.noarch 0:36.5.0-1.el6 will be installed
---> Package rh-python36-runtime.x86_64 0:2.0-1.el6 will be installed
---> Package scl-utils-build.x86_64 0:20120927-29.el6_9 will be installed
--> Running transaction check
---> Package gcc-objc++.x86_64 0:4.4.7-17.el6 will be updated
---> Package gcc-objc++.x86_64 0:4.4.7-23.el6 will be an update
---> Package libgfortran.x86_64 0:4.4.7-17.el6 will be updated
---> Package libgfortran.x86_64 0:4.4.7-23.el6 will be an update
---> Package libgnat.x86_64 0:4.4.7-17.el6 will be updated
---> Package libgnat.x86_64 0:4.4.7-23.el6 will be an update
---> Package libgnat-devel.x86_64 0:4.4.7-17.el6 will be updated
---> Package libgnat-devel.x86_64 0:4.4.7-23.el6 will be an update
---> Package libobjc.x86_64 0:4.4.7-17.el6 will be updated
---> Package libobjc.x86_64 0:4.4.7-23.el6 will be an update
---> Package libstdc++.x86_64 0:4.4.7-17.el6 will be updated
---> Package libstdc++.x86_64 0:4.4.7-23.el6 will be an update
---> Package libstdc++-devel.x86_64 0:4.4.7-17.el6 will be updated
---> Package libstdc++-devel.x86_64 0:4.4.7-23.el6 will be an update
--> Finished Dependency Resolution
Dependencies Resolved
================================================================================
Package Arch Version Repository Size
================================================================================
Installing:
libffi-devel x86_64 3.0.5-3.2.el6 base 18 k
redhat-rpm-config noarch 9.0.3-51.el6.centos base 60 k
rh-python36-python x86_64 3.6.9-2.el6 centos-sclo-rh 55 k
rh-python36-python-devel x86_64 3.6.9-2.el6 centos-sclo-rh 918 k
rh-python36-python-virtualenv noarch 15.1.0-2.el6 centos-sclo-rh 1.8 M
Updating:
ca-certificates noarch 2019.2.32-65.1.el6_10
updates 944 k
gcc x86_64 4.4.7-23.el6 base 10 M
openssl x86_64 1.0.1e-58.el6_10 updates 1.5 M
openssl-devel x86_64 1.0.1e-58.el6_10 updates 1.2 M
Installing for dependencies:
rh-python36-python-libs x86_64 3.6.9-2.el6 centos-sclo-rh 7.5 M
rh-python36-python-pip noarch 9.0.1-2.el6 centos-sclo-rh 1.8 M
rh-python36-python-setuptools noarch 36.5.0-1.el6 centos-sclo-rh 584 k
rh-python36-runtime x86_64 2.0-1.el6 centos-sclo-rh 1.0 M
scl-utils-build x86_64 20120927-29.el6_9 base 17 k
Updating for dependencies:
cpp x86_64 4.4.7-23.el6 base 3.7 M
gcc-c++ x86_64 4.4.7-23.el6 base 4.7 M
gcc-gfortran x86_64 4.4.7-23.el6 base 4.7 M
gcc-gnat x86_64 4.4.7-23.el6 base 8.7 M
gcc-objc x86_64 4.4.7-23.el6 base 3.7 M
gcc-objc++ x86_64 4.4.7-23.el6 base 4.0 M
libgcc x86_64 4.4.7-23.el6 base 104 k
libgfortran x86_64 4.4.7-23.el6 base 268 k
libgnat x86_64 4.4.7-23.el6 base 912 k
libgnat-devel x86_64 4.4.7-23.el6 base 3.3 M
libgomp x86_64 4.4.7-23.el6 base 135 k
libobjc x86_64 4.4.7-23.el6 base 93 k
libstdc++ x86_64 4.4.7-23.el6 base 296 k
libstdc++-devel x86_64 4.4.7-23.el6 base 1.6 M
Transaction Summary
================================================================================
Install 10 Package(s)
Upgrade 18 Package(s)
Total download size: 64 M
Is this ok [y/N]: y
Downloading Packages:
(1/28): ca-certificates-2019.2.32-65.1.el6_10.noarch.rpm | 944 kB 00:00
(2/28): cpp-4.4.7-23.el6.x86_64.rpm | 3.7 MB 00:02
(3/28): gcc-4.4.7-23.el6.x86_64.rpm | 10 MB 00:08
(4/28): gcc-c++-4.4.7-23.el6.x86_64.rpm | 4.7 MB 00:04
(5/28): gcc-gfortran-4.4.7-23.el6.x86_64.rpm | 4.7 MB 00:03
^A(6/28): gcc-gnat-4.4.7 (43%) 36% [==== ] 527 kB/s | 3.2 MB 00:10 ET(6/28): gcc-gnat-4.4.7-23.el6.x86_64.rpm | 8.7 MB 00:06
(7/28): gcc-objc-4.4.7-23.el6.x86_64.rpm | 3.7 MB 00:00
(8/28): gcc-objc++-4.4.7-23.el6.x86_64.rpm | 4.0 MB 00:02
(9/28): libffi-devel-3.0.5-3.2.el6.x86_64.rpm | 18 kB 00:00
(10/28): libgcc-4.4.7-23.el6.x86_64.rpm | 104 kB 00:00
(11/28): libgfortran-4.4.7-23.el6.x86_64.rpm | 268 kB 00:00
(12/28): libgnat-4.4.7-23.el6.x86_64.rpm | 912 kB 00:01
(13/28): libgnat-devel-4.4.7-23.el6.x86_64.rpm | 3.3 MB 00:03
(14/28): libgomp-4.4.7-23.el6.x86_64.rpm | 135 kB 00:00
(15/28): libobjc-4.4.7-23.el6.x86_64.rpm | 93 kB 00:00
(16/28): libstdc++-4.4.7-23.el6.x86_64.rpm | 296 kB 00:00
(17/28): libstdc++-devel-4.4.7-23.el6.x86_64.rpm | 1.6 MB 00:00
(18/28): openssl-1.0.1e-58.el6_10.x86_64.rpm | 1.5 MB 00:00
(19/28): openssl-devel-1.0.1e-58.el6_10.x86_64.rpm | 1.2 MB 00:01
(20/28): redhat-rpm-config-9.0.3-51.el6.centos.noarch.rp | 60 kB 00:00
(21/28): rh-python36-python-3.6.9-2.el6.x86_64.rpm | 55 kB 00:00
(22/28): rh-python36-python-devel-3.6.9-2.el6.x86_64.rpm | 918 kB 00:01
(23/28): rh-python36-python-libs-3.6.9-2.el6.x86_64.rpm | 7.5 MB 00:03
(24/28): rh-python36-python-pip-9.0.1-2.el6.noarch.rpm | 1.8 MB 00:00
(25/28): rh-python36-python-setuptools-36.5.0-1.el6.noar | 584 kB 00:00
(26/28): rh-python36-python-virtualenv-15.1.0-2.el6.noar | 1.8 MB 00:02
(27/28): rh-python36-runtime-2.0-1.el6.x86_64.rpm | 1.0 MB 00:01
(28/28): scl-utils-build-20120927-29.el6_9.x86_64.rpm | 17 kB 00:00
--------------------------------------------------------------------------------
Total 1.4 MB/s | 64 MB 00:46
warning: rpmts_HdrFromFdno: Header V4 RSA/SHA1 Signature, key ID f2ee9d55: NOKEY
Retrieving key from file:///etc/pki/rpm-gpg/RPM-GPG-KEY-CentOS-SIG-SCLo
Importing GPG key 0xF2EE9D55:
Userid : CentOS SoftwareCollections SIG (https://wiki.centos.org/SpecialInterestGroup/SCLo) <security@centos.org>
Package: centos-release-scl-rh-2-4.el6.centos.noarch (@extras)
From : /etc/pki/rpm-gpg/RPM-GPG-KEY-CentOS-SIG-SCLo
Is this ok [y/N]y
Running rpm_check_debug
Running Transaction Test
Transaction Test Succeeded
Running Transaction
Updating : libgcc-4.4.7-23.el6.x86_64 1/46
Updating : libgnat-4.4.7-23.el6.x86_64 2/46
Updating : libstdc++-4.4.7-23.el6.x86_64 3/46
Installing : rh-python36-runtime-2.0-1.el6.x86_64 4/46
Updating : libstdc++-devel-4.4.7-23.el6.x86_64 5/46
Updating : libgnat-devel-4.4.7-23.el6.x86_64 6/46
Updating : libobjc-4.4.7-23.el6.x86_64 7/46
Updating : cpp-4.4.7-23.el6.x86_64 8/46
Updating : ca-certificates-2019.2.32-65.1.el6_10.noarch 9/46
Updating : openssl-1.0.1e-58.el6_10.x86_64 10/46
Installing : rh-python36-python-libs-3.6.9-2.el6.x86_64 11/46
Installing : rh-python36-python-3.6.9-2.el6.x86_64 12/46
Installing : rh-python36-python-setuptools-36.5.0-1.el6.noarch 13/46
Installing : rh-python36-python-pip-9.0.1-2.el6.noarch 14/46
Updating : libgfortran-4.4.7-23.el6.x86_64 15/46
Updating : libgomp-4.4.7-23.el6.x86_64 16/46
Updating : gcc-4.4.7-23.el6.x86_64 17/46
Updating : gcc-objc-4.4.7-23.el6.x86_64 18/46
Updating : gcc-c++-4.4.7-23.el6.x86_64 19/46
Installing : redhat-rpm-config-9.0.3-51.el6.centos.noarch 20/46
Installing : scl-utils-build-20120927-29.el6_9.x86_64 21/46
Installing : rh-python36-python-devel-3.6.9-2.el6.x86_64 22/46
Installing : rh-python36-python-virtualenv-15.1.0-2.el6.noarch 23/46
Updating : gcc-objc++-4.4.7-23.el6.x86_64 24/46
Updating : gcc-gnat-4.4.7-23.el6.x86_64 25/46
Updating : gcc-gfortran-4.4.7-23.el6.x86_64 26/46
Updating : openssl-devel-1.0.1e-58.el6_10.x86_64 27/46
Installing : libffi-devel-3.0.5-3.2.el6.x86_64 28/46
Cleanup : gcc-gnat-4.4.7-17.el6.x86_64 29/46
Cleanup : gcc-gfortran-4.4.7-17.el6.x86_64 30/46
Cleanup : gcc-objc++-4.4.7-17.el6.x86_64 31/46
Cleanup : libgnat-devel-4.4.7-17.el6.x86_64 32/46
Cleanup : openssl-devel-1.0.1e-48.el6_8.3.x86_64 33/46
Cleanup : gcc-c++-4.4.7-17.el6.x86_64 34/46
Cleanup : gcc-objc-4.4.7-17.el6.x86_64 35/46
Cleanup : libstdc++-devel-4.4.7-17.el6.x86_64 36/46
Cleanup : gcc-4.4.7-17.el6.x86_64 37/46
Cleanup : libstdc++-4.4.7-17.el6.x86_64 38/46
Cleanup : libobjc-4.4.7-17.el6.x86_64 39/46
Cleanup : openssl-1.0.1e-48.el6_8.3.x86_64 40/46
Cleanup : libgnat-4.4.7-17.el6.x86_64 41/46
Cleanup : ca-certificates-2015.2.6-65.0.1.el6_7.noarch 42/46
Cleanup : libgcc-4.4.7-17.el6.x86_64 43/46
Cleanup : cpp-4.4.7-17.el6.x86_64 44/46
Cleanup : libgomp-4.4.7-17.el6.x86_64 45/46
Cleanup : libgfortran-4.4.7-17.el6.x86_64 46/46
Verifying : libobjc-4.4.7-23.el6.x86_64 1/46
Verifying : rh-python36-python-devel-3.6.9-2.el6.x86_64 2/46
Verifying : gcc-4.4.7-23.el6.x86_64 3/46
Verifying : libffi-devel-3.0.5-3.2.el6.x86_64 4/46
Verifying : gcc-objc-4.4.7-23.el6.x86_64 5/46
Verifying : libstdc++-devel-4.4.7-23.el6.x86_64 6/46
Verifying : gcc-objc++-4.4.7-23.el6.x86_64 7/46
Verifying : rh-python36-python-setuptools-36.5.0-1.el6.noarch 8/46
Verifying : rh-python36-python-libs-3.6.9-2.el6.x86_64 9/46
Verifying : redhat-rpm-config-9.0.3-51.el6.centos.noarch 10/46
Verifying : libgnat-devel-4.4.7-23.el6.x86_64 11/46
Verifying : libgnat-4.4.7-23.el6.x86_64 12/46
Verifying : libgomp-4.4.7-23.el6.x86_64 13/46
Verifying : libgfortran-4.4.7-23.el6.x86_64 14/46
Verifying : gcc-c++-4.4.7-23.el6.x86_64 15/46
Verifying : rh-python36-python-3.6.9-2.el6.x86_64 16/46
Verifying : rh-python36-runtime-2.0-1.el6.x86_64 17/46
Verifying : openssl-1.0.1e-58.el6_10.x86_64 18/46
Verifying : ca-certificates-2019.2.32-65.1.el6_10.noarch 19/46
Verifying : gcc-gnat-4.4.7-23.el6.x86_64 20/46
Verifying : gcc-gfortran-4.4.7-23.el6.x86_64 21/46
Verifying : scl-utils-build-20120927-29.el6_9.x86_64 22/46
Verifying : rh-python36-python-virtualenv-15.1.0-2.el6.noarch 23/46
Verifying : openssl-devel-1.0.1e-58.el6_10.x86_64 24/46
Verifying : libstdc++-4.4.7-23.el6.x86_64 25/46
Verifying : cpp-4.4.7-23.el6.x86_64 26/46
Verifying : libgcc-4.4.7-23.el6.x86_64 27/46
Verifying : rh-python36-python-pip-9.0.1-2.el6.noarch 28/46
Verifying : gcc-objc-4.4.7-17.el6.x86_64 29/46
Verifying : libobjc-4.4.7-17.el6.x86_64 30/46
Verifying : libstdc++-4.4.7-17.el6.x86_64 31/46
Verifying : cpp-4.4.7-17.el6.x86_64 32/46
Verifying : gcc-gnat-4.4.7-17.el6.x86_64 33/46
Verifying : libgnat-4.4.7-17.el6.x86_64 34/46
Verifying : libgfortran-4.4.7-17.el6.x86_64 35/46
Verifying : libgcc-4.4.7-17.el6.x86_64 36/46
Verifying : openssl-1.0.1e-48.el6_8.3.x86_64 37/46
Verifying : libgnat-devel-4.4.7-17.el6.x86_64 38/46
Verifying : libstdc++-devel-4.4.7-17.el6.x86_64 39/46
Verifying : gcc-c++-4.4.7-17.el6.x86_64 40/46
Verifying : gcc-objc++-4.4.7-17.el6.x86_64 41/46
Verifying : openssl-devel-1.0.1e-48.el6_8.3.x86_64 42/46
Verifying : gcc-gfortran-4.4.7-17.el6.x86_64 43/46
Verifying : gcc-4.4.7-17.el6.x86_64 44/46
Verifying : libgomp-4.4.7-17.el6.x86_64 45/46
Verifying : ca-certificates-2015.2.6-65.0.1.el6_7.noarch 46/46
Installed:
libffi-devel.x86_64 0:3.0.5-3.2.el6
redhat-rpm-config.noarch 0:9.0.3-51.el6.centos
rh-python36-python.x86_64 0:3.6.9-2.el6
rh-python36-python-devel.x86_64 0:3.6.9-2.el6
rh-python36-python-virtualenv.noarch 0:15.1.0-2.el6
Dependency Installed:
rh-python36-python-libs.x86_64 0:3.6.9-2.el6
rh-python36-python-pip.noarch 0:9.0.1-2.el6
rh-python36-python-setuptools.noarch 0:36.5.0-1.el6
rh-python36-runtime.x86_64 0:2.0-1.el6
scl-utils-build.x86_64 0:20120927-29.el6_9
Updated:
ca-certificates.noarch 0:2019.2.32-65.1.el6_10
gcc.x86_64 0:4.4.7-23.el6
openssl.x86_64 0:1.0.1e-58.el6_10
openssl-devel.x86_64 0:1.0.1e-58.el6_10
Dependency Updated:
cpp.x86_64 0:4.4.7-23.el6 gcc-c++.x86_64 0:4.4.7-23.el6
gcc-gfortran.x86_64 0:4.4.7-23.el6 gcc-gnat.x86_64 0:4.4.7-23.el6
gcc-objc.x86_64 0:4.4.7-23.el6 gcc-objc++.x86_64 0:4.4.7-23.el6
libgcc.x86_64 0:4.4.7-23.el6 libgfortran.x86_64 0:4.4.7-23.el6
libgnat.x86_64 0:4.4.7-23.el6 libgnat-devel.x86_64 0:4.4.7-23.el6
libgomp.x86_64 0:4.4.7-23.el6 libobjc.x86_64 0:4.4.7-23.el6
libstdc++.x86_64 0:4.4.7-23.el6 libstdc++-devel.x86_64 0:4.4.7-23.el6
Complete!
Creating virtual environment...
Installing Python packages...
Installation succeeded.
Saving debug log to /var/log/letsencrypt/letsencrypt.log
How would you like to authenticate with the ACME CA?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: Spin up a temporary webserver (standalone)
2: Place files in webroot directory (webroot)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 1
Plugins selected: Authenticator standalone, Installer None
Enter email address (used for urgent renewal and security notices) (Enter 'c' to
cancel): hnamju@gmail.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must
agree in order to register with the ACME server at
https://acme-v02.api.letsencrypt.org/directory
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(A)gree/(C)ancel: A
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing to share your email address with the Electronic Frontier
Foundation, a founding partner of the Let's Encrypt project and the non-profit
organization that develops Certbot? We'd like to send you email about our work
encrypting the web, EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for www.jobtoy.com
Cleaning up challenges
Problem binding to port 80: Could not bind to IPv4 or IPv6.
IMPORTANT NOTES:
- Your account credentials have been saved in your Certbot
configuration directory at /etc/letsencrypt. You should make a
secure backup of this folder now. This configuration directory will
also contain certificates and private keys obtained by Certbot so
making regular backups of this folder is ideal.
[root@labj ~]#
검색결과
하지만 이번에는 아래와 같은 오류가 나게 된다.
produced an unexpected error: Problem binding to port 443: Could not bind to IPv4 or IPv6.. Skipping.
All renewal attempts failed. The following certs could not be renewed
갱신하려는 인증서를 이미 nginx 서버에서 사용중이기 때문에 갱신이 불가능하다는 내용이다.
다시 함
#certbot-auto certonly -a webroot ?renew-by-default ?agree-tos -m hnamju@gmail.com -w [DocumentRoot 경로] -d [도메인] -d [도메인2..] ?rsa-key-size 4096
[root@labj letsencrypt]# certbot-auto certonly -d www.jobtoy.com
Saving debug log to /var/log/letsencrypt/letsencrypt.log
How would you like to authenticate with the ACME CA?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: Spin up a temporary webserver (standalone)
2: Place files in webroot directory (webroot)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 1
Plugins selected: Authenticator standalone, Installer None
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for www.jobtoy.com
Waiting for verification...
Cleaning up challenges
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/www.jobtoy.com/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/www.jobtoy.com/privkey.pem
Your cert will expire on 2020-06-26. To obtain a new or tweaked
version of this certificate in the future, simply run certbot-auto
again. To non-interactively renew *all* of your certificates, run
"certbot-auto renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
[root@labj letsencrypt]#
[root@labj letsencrypt]# pwd
/etc/letsencrypt
[root@labj letsencrypt]# ls /etc/letsencrypt/live
README www.jobtoy.com
[root@labj letsencrypt]# ls /etc/letsencrypt/live/www.jobtoy.com/
cert.pem chain.pem fullchain.pem privkey.pem README
[root@labj letsencrypt]#
[root@labj letsencrypt]# nano /etc/letsencrypt/live/www.jobtoy.com/README
This directory contains your keys and certificates.
`privkey.pem` : the private key for your certificate.
`fullchain.pem`: the certificate file used in most server software.
`chain.pem` : used for OCSP stapling in Nginx >=1.3.7.
`cert.pem` : will break many server configurations, and should not be used
without reading further documentation (see link below).
WARNING: DO NOT MOVE OR RENAME THESE FILES!
Certbot expects these files to remain in this location in order
to function properly!
We recommend not moving these files. For more information, see the Certbot
User Guide at https://certbot.eff.org/docs/using.html#where-are-my-certificates.
참고 사이트
https://minddong.tistory.com/20
http://macaronics.net/index.php/m01/spring/view/1586
https://iwan2fly.tistory.com/203
https://iwan2fly.tistory.com/203
https://www.enteroa.com/2018/05/16/lets-encrypt-%EC%97%90%EC%84%9C-%EC%83%9D%EC%84%B1%EB%90%9C-pem-%EC%9D%B8%EC%A6%9D%EC%84%9C%EB%A5%BC-tomcat%EC%97%90%EC%84%9C-%EC%82%AC%EC%9A%A9-%ED%95%98%EA%B8%B0/
https://minddong.tistory.com/20
https://computingforgeeks.com/tomcat-7-with-letsencrypt-ssl-certificate/
https://idchowto.com/?p=47592
----------------------------------------------------------------------
완료 이전 3개월 후에 다시 접속하여 다음 명령을 넣어 봄
----------------------------------------------------------------------
'linux' 카테고리의 다른 글
| [리눅스 민트] 기본 설치 내용 (0) | 2019.03.24 |
|---|---|
| [리눅스 민트] 버전 확인하기 (0) | 2019.03.20 |
| [리눅스민트] 리눅스 민트 cura 3.1.0 설치 및 설정하기 (0) | 2019.03.19 |
| [리눅스민트] cura 설치하기 (0) | 2019.03.07 |
| [리눅스 민트] 메뉴 추가하기 (0) | 2019.02.26 |